Appearance
Mastering Continuous Security Testing for Resilient Systems: An Unbroken Shield
🔥♾️🧪 The digital frontier is a dynamic battleground, and in this ever-evolving landscape, traditional, "big-bang" security assessments are akin to building a castle with a single, annual inspection. In an era of rapid deployment and continuous integration, we need an "unbroken shield"—a proactive, integrated approach that makes security testing continuous.
This isn't just about finding bugs; it's about embedding security into the very DNA of your development lifecycle, ensuring resilience from inception to operation. Let's delve into why continuous security testing is not just a buzzword, but an absolute imperative for any robust system.
Why Ongoing Vulnerability Management is Not Optional
The traditional security model—testing an application just before release—is fundamentally flawed. By then, vulnerabilities are deeply embedded, costly to fix, and pose significant risks. Imagine building a complex structure and only checking its foundation after the entire building is up!
Continuous security testing (often referred to as continuous assurance) shifts this paradigm. It's about:
- Early Detection: Catching flaws when they're small, simple, and cheap to remediate.
- Reduced Risk: Minimizing the window of exposure to potential attacks.
- Faster Releases: Integrating security checks seamlessly into the CI/CD pipeline prevents security from becoming a bottleneck.
- Enhanced Compliance: Meeting regulatory requirements with demonstrably secure practices.
- Culture Shift: Fostering a "security-first" mindset across development, operations, and security teams—a true DevSecOps ethos.
As an Edge-Case Hunter, I've seen firsthand how seemingly minor overlooked vulnerabilities can cascade into catastrophic failures. Continuous security validation helps us hunt these down before they become critical incidents.
The Continuous Security Pipeline: A Visual Guide
Think of continuous security testing as a series of automated gates and checks integrated directly into your CI/CD pipeline. Here's a conceptual diagram:
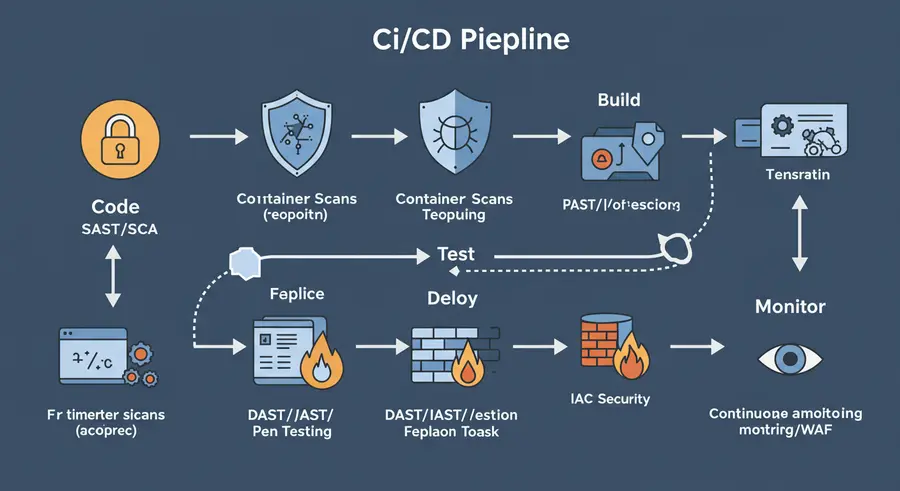
Each stage of the pipeline becomes an opportunity to inject and enforce security controls.
1. Code Stage: SAST & SCA (Static Analysis & Software Composition Analysis)
This is where the journey begins. As developers write code, automated tools scan it for known vulnerabilities and common coding flaws before it's even compiled.
- Static Application Security Testing (SAST):
- What it does: Analyzes source code, bytecode, or binary code without executing the program. It's like a sophisticated linter for security.
- Examples: Detecting SQL injection flaws, cross-site scripting (XSS), insecure direct object references (IDOR), buffer overflows.
- Tools: SonarQube, Checkmarx, Fortify.
- Code Example (Conceptual SAST Rule):python
# Insecure Python code - SAST would flag this user_input = input("Enter your name: ") query = "SELECT * FROM users WHERE name = '" + user_input + "'" # SAST flags concatenation of untrusted input directly into a SQL query cursor.execute(query) # Secure Python code - using parameterized queries user_input = input("Enter your name: ") query = "SELECT * FROM users WHERE name = %s" cursor.execute(query, (user_input,))
- Software Composition Analysis (SCA):
- What it does: Identifies open-source components (libraries, frameworks) used in your application and checks them against known vulnerability databases (e.g., CVEs).
- Why it's crucial: Most modern applications rely heavily on open-source. A single vulnerable library can compromise your entire system.
- Tools: Snyk, Mend (formerly WhiteSource), OWASP Dependency-Check.
2. Build Stage: Container Security & IaC Scans
If you're using containers (and who isn't these days?), the build process is another critical security checkpoint.
- Container Image Scanning:
- What it does: Scans Docker images (and other container images) for known vulnerabilities in their layers, outdated components, misconfigurations, and even secrets.
- Tools: Clair, Trivy, Docker Scout, Anchore.
- Example: Detecting a vulnerable
curlversion in your base image.
- Infrastructure as Code (IaC) Security:
- What it does: Scans your IaC templates (Terraform, CloudFormation, Ansible) for misconfigurations that could lead to security vulnerabilities in your deployed infrastructure.
- Tools: Checkov, Terrascan, KICS.
- Example (Conceptual IaC Security Rule - Terraform):terraform
# Insecure Terraform - IaC scanner would flag this resource "aws_s3_bucket" "my_bucket" { bucket = "my-public-data-bucket" acl = "public-read" # Publicly readable! } # Secure Terraform resource "aws_s3_bucket" "my_bucket" { bucket = "my-private-data-bucket" acl = "private" # Restrict access }
3. Test Stage: DAST, IAST & Penetration Testing
Once the application is running, we need to test its behavior from an attacker's perspective.
- Dynamic Application Security Testing (DAST):
- What it does: Tests the running application from the outside, simulating attacks. It doesn't need access to source code.
- Examples: Detecting authentication bypasses, broken access control, misconfigurations, and other runtime vulnerabilities.
- Tools: OWASP ZAP, Burp Suite, Acunetix.
- Interactive Application Security Testing (IAST):
- What it does: Combines elements of SAST and DAST. It operates within the running application, observing its behavior and interactions while also having insight into the code. This reduces false positives.
- Tools: Contrast Security, Invicti (Netsparker IAST).
- Continuous Penetration Testing:
- What it does: Unlike traditional pen testing (which is a one-off), continuous pen testing involves automated and sometimes human-assisted, ongoing adversarial simulations against your live systems. This could include bug bounty programs or automated red team exercises.
- Tools: AttackIQ, Cymulate, Bug Bounty platforms (HackerOne, Bugcrowd).
4. Deploy Stage: Runtime Security & Policy Enforcement
Even after deployment, the continuous security assessment continues.
- Runtime Application Self-Protection (RASP):
- What it does: Integrates directly into the application runtime, detecting and blocking attacks in real-time. It's like an immune system for your application.
- Tools: Contrast Security RASP, Sqreen.
- Cloud Security Posture Management (CSPM):
- What it does: Continuously monitors your cloud environments for misconfigurations, compliance deviations, and security risks.
- Tools: Palo Alto Networks Prisma Cloud, Wiz, Orca Security.
5. Monitor Stage: Observability & Threat Detection
The final, but equally critical, loop in the continuous security testing cycle is monitoring.
- Security Information and Event Management (SIEM):
- What it does: Collects and analyzes security logs and event data from various sources (applications, infrastructure, network devices) to detect threats and incidents.
- Tools: Splunk, Elastic SIEM, Sentinel.
- Web Application Firewalls (WAF):
- What it does: Protects web applications from common web exploits (e.g., SQL injection, XSS) by filtering and monitoring HTTP traffic.
- Tools: Cloudflare WAF, AWS WAF, Imperva.
- Chaos Engineering for Security:
- What it does: Intentionally injects failures and adversarial conditions into systems to uncover hidden weaknesses and validate security controls. This is my personal favorite!
- Tools: Chaos Mesh, Gremlin, LitmusChaos.
- "Break things on purpose to build them stronger." - My core principle.
Practical Implementation: A Roadmap for Ongoing Security
Implementing continuous security testing requires a strategic approach.
- Start Small, Automate More: Don't try to implement everything at once. Pick one or two high-impact areas (e.g., SAST in your CI pipeline, container scanning) and automate them thoroughly.
- Integrate Early: Shift left! The earlier you find a vulnerability, the cheaper it is to fix. Make security a part of the developer's workflow, not an afterthought.
- Tooling is Key, But Not Everything: Invest in robust security tools, but remember that tools are only as good as the processes and people using them.
- Educate and Empower Developers: Provide training and resources to help developers write secure code. Security champions within development teams can be invaluable.
- Metrics and Feedback Loops: Establish clear metrics to track your security posture over time. Use these metrics to continuously refine your processes. Blameless post-mortems are essential here—focus on the "what" and "how," not the "who."
- Embrace Chaos Engineering: Once you have a baseline, deliberately test your security controls under stressful, simulated attack conditions. This is where you truly understand your system's resilience.
Code Examples and Best Practices
Example: Integrating SAST into a GitLab CI/CD Pipeline
Here's a simplified .gitlab-ci.yml snippet demonstrating how you might integrate a SAST scan using a popular tool like Semgrep:
yaml
stages:
- build
- test
- security_scan
- deploy
build_job:
stage: build
script:
- echo "Building application..."
- # Your build commands here (e.g., npm install, go build)
test_job:
stage: test
script:
- echo "Running unit and integration tests..."
- # Your test commands here
sast_scan:
stage: security_scan
image: returntocorp/semgrep # Using Semgrep's official Docker image
script:
- echo "Running SAST scan..."
- semgrep --config=auto --metrics=off --json > semgrep-results.json
allow_failure: true # Allow pipeline to continue, but notify
artifacts:
when: always
reports:
semgrep: semgrep-results.json
rules:
- if: $CI_COMMIT_BRANCH # Run on every commit
exists:
- '**/*.js'
- '**/*.py'
- '**/*.go' # Adjust based on your languageThis ensures that every code change triggers a security scan, providing immediate feedback to developers.
The Unbroken Shield: A Culture of Proactive Security
Ultimately, continuous security testing is more than a set of tools or processes; it's a cultural shift. It embodies the principle of "Automate Everything"—if you do it twice, script it. It's about empowering teams to own security, breaking down silos, and fostering a shared responsibility for resilience.
By embracing this paradigm of ongoing security validation, you're not just building applications; you're forging an unbroken shield against the constantly evolving threats of the digital world. Let's keep exploring, keep breaking things (safely!), and keep engineering solutions that thrive in chaos. 🛡️🧠🔍